I did and I used this summary with some bullets and some parts of text extracted from AWS papers and from come online courses like cloud guru, linux academy, udemy. To study concepts about AWS Networking.
I hope it could be useful to someone.
OSI Model:
AWS Responsibility:
- Physical (CAT5, fiber optical cable)
- Data Link (MAC)
Customer Responsibility :
- Network (IP,ARP)
- Transport (TCP)
- Session (Setup, Negotiation,Teardown )
- Application (web browser)
Unicast: Communication in which a frame is sent from a host and addressed to a specific destination.
Multicast: Communication in which a frame is sent to a specific group of devices or clients.
Broadcast: Communication in which a frame is sent from one address to all other addresses.
TCP:
- connection based, stateful, acknowledge
- After everything I say, I want you to confirm that you receive it
- Ex: web, email, file transfer
UDP:
- Connectionless, stateless, simple no retransmission delays.
- I’m going to start talking and its ok if you miss some words
- Ex: Streaming media, DNS
ICMP:
- Used by network devices to exchange info
- We routers can keep in touch about the health of the network using our own language
- Ex: traceroute, ping
Ephemeral Ports:
Short-lived transport protocol used in IP communications
Above the "well-known” IP ports (above 1024)
Dynamic ports
Suggested range is 49152 to 65535 but
Linux kernels generally use 32568 to 61000
Windows plataformas default from 1025
NACL and security groups implications
AWS Managed VPN
- AWS managed IpSec VPN connection over your existing internet
- Quick and usually simple way to establish secure tunnelled connection to a VPC
- Redundant link for Direct connect or other VPC VPN
- Support to Static routes or BGP peering and routing
- Dependent on your internet connection
Limitations:
- Network latency, variability, and availability are dependent on internet conditions
- Customer managed endpoint is responsible for implementing redundancy and failover (if required)
- Customer device must support single-hop BGP (when leveraging BGP for dynamic routing)
Direct Connect
- Dedicate network connection over private lines straight int AWS backbone
- Used when required a big pipe int AWS, lots of resource and service being provided on AWS to tour corporate users
- More predictable network perfomance, potential bandwidth cost reduction, up to 10Gbps provisioned connections, supports BGP peering and routing.
- Work with your existing Data network Provider, create virtual interfaces (VIF) to connect to VPCs (privates VIF ) or others AWS services like S3 or Glacier (public VIF)
Limitations:
- May required additional telecom and hosting provider relationships and/or new network circuits.
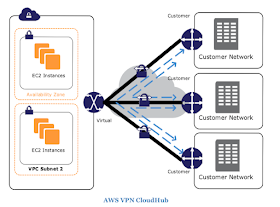
VPN Cloud Hub
- Connect location in a Hub and Spoke manner using AWS’s Virtual private gateway.
- Used when is necessary has link remote offices for backup or primary WAN access to AWS resources or each others.
- Reuses existing internet connection, Supports BGP route to direct traffic for example, use MPLS first then CloudHub VPN as Backup.
- Depends on the internet connection, no inherent redundancy.
- Assing multiple Customer Gateway to a Virtual Private gateway, each whit their own BGP ASN and unique IP range.
Limitations:
- Network latency, variability, and availability are dependent on the internet
- User managed branch office endpoints are responsible for implementing redundancy and failover (if required)
AWS Direct Connect + VPN
- Use Case: IPsec VPN connection over private lines
- Advantages are the same as the previous option with the addition of a secure IPsec VPN connection
Limitations:
- Same as the previous option with a little additional VPN complexity
Software VPN
- You provide your own VPN endpoint and software.
- You must manage both ends of the VPN connection for compliance reasons or you want to use a VPN option not supports by AWS.
- Ultimate flexibility and manageability.
- You must design for any needed redundancy across the whole chain.
- Install VPN via Marketplace appliance or on an EC2 instance.
Limitations:
- Customer is responsible for implementing HA (high availability) solutions for all VPN endpoints (if required)
Transit VPC
Software appliance- based VPN connection with hub VPC
AWS managed IPsec VPN connection for spoke VPC connection
Common strategy for connection geographically disperse VPCs and locations in order to create a global network transit center.
Used when locations and VPC-deployed assets across multiple regions that need to communication with one another.
Ultimate flexibility and manageability but also AWS- managed VPN hub-and-spoke between VPCs.
You must design for any needed redundancy across the whole chain.
Provides like cisco , Juniper Network and Riverbed have offering which work with their equipments and AWS VPC.
VPC peering
AWS provided network connectivity between two VPCs.
Used when is necessary multiple VPCs need to communicate or access each other resources.
Uses AWS backbone without touching the internet.
If A is connected to B and B is connected to C, A cannot talk with C via B. (Transitive peering not supported)
VPC peering requested is made, accepter accepter request (either within Account or acros accounts).
Leverages AWS networking infrastructure
Does not rely on VPN instances or a separate piece of physical hardware
No single point of failure No bandwidth bottleneck
PrivateLink
AWS PrivateLink network connectivity between VPCs and/or AWS services using interfaces endpoints.
Used when is necessary keep private subnet truly private by using the AWS backbone to reach other services rather that the public internet.
Redundant: uses AWS backbone
As of October 2018, they can be accessed over inter-region VPC peering.
Create endpoint for needed AWS or marketplace service in all needed subnets, access via the provided DNS hostname.
Limitation:
VPC Endpoint services only available in AWS region in which they are created.
VPC Endpoint
It can be divided into two groups:
Interface Endpoint:
Elastic network interface with an Private IP
Uses DNS entries to redirect traffic.
Could be used on API Gateway, cloudFormation, Cloud watch, etc.
Securing with security groups.
Gateway Endepoints:
A gateway that is a target for a specific route.
Uses prefix list in the route table to redirect traffic.
Cloud be used on S3, DynamoDB.
Securing with VPC Endpoint Polices.
NO VPC Endpoint:
VPC Endpoint :
- Internet gateway
- Egress-Only Internet Gateway
- NAT Instance
- Nat Gateway
Internet gateway
Horizontally scaled, redundant and highly available component that allows communication between your VPC and the internet.
No available risk or bandwidth constraints.
If you subnet is associated with a route to the internet, the it is a public subnet.
Suports IVP4 and IPV6
Purpose 1: Provide route table target for internet bound traffic.
Purpose 2: Perform NAT for instance with public IP addresses.
Does not performance NAT for instances with privates IP’s only.
Egress-Only Internet Gateway
IPV6 address are globally unique and are therefore public by default.
Provides outbound internet access for IPV6 address instances.
Prevents inbound access to those IPV6 instances.
Stateful forwards traffic from instances to internet and the sends back the response.
Must create a custom route for ::/0 to the Egress-Only internet gateway.
Use Egress-Only internet Gateway instead of NAT for IPV6.
Allow IPV6 base on traffic within a VPC to access the internet, whilst denying any internet based resources, the possibility of initiating a connection back into the VPC.
NAT Instance
Ec2 instance from a special AWS provided AMI
Translate traffic from many private IP instance to a single public IP and back.
Doesn’t allow public internet initiate connections into private instances.
Not support fot IPV6(use Egress-Only internet gateway )
NAT instances must live o a public subnet with route to Internet Gateway.
Private instances in private subnets must have route to the NAT instances, usually the default route destination of 0.0.0.0/0
NAT Gateway
Fully managed NAT services that replaces need for NAT instances on EC2.
Must be created in a public subnet.
Uses an elastic IP for public IP for the life of the Gateway.
Private instances in private subnets must have route to the NAT instances, usually the default route destination of 0.0.0.0/0
Create in specific AZ redundancy, create NAT gateway in each AZ with routes for private subnet to use the local Gateway.
Up to 5Gbps bandwidth that can scale up to 45Gbps.
Can’t use a NAT Gateway to access VPC peering, VPN or Direct connect, so be sure to include specific route to those in your route table
Advices:
Only two componentes allow VPC to internet communication using IPV6 address and those are “Internet gateway”(inbound) and “Egress-Only Internet Gateway “(outbund). NAT Instance and NAT Gateway explicitly don’t support IPV6 traffic and a Direct Connection carries data between a Data center and an AWS VPC, but doesn’t travel over the internet.
NAT Gateway vs NAT Instance
Availability :
NAT Gateway -> High availability within AZ
NAT Instance -> On your own
Bandwidth:
NAT Gateway -> Up to 45 Gbps
NAT Instance -> Depends on bandwidth of instance type
Maintenance:
NAT Gateway -> Managed by AWS
NAT Instance -> On your own
Performance:
NAT Gateway -> Optimised for NAT
NAT Instance -> Amazon Linux AMI configured to perform NAT
Public IP:
NAT Gateway -> Elastic IP that can not be detached
NAT Instance -> Elastic IP that can be detached.
Security Groups:
NAT Gateway -> Cannot be associate with NAT Gateway
NAT Instance -> Can use Security Groups
Bastion Server:
NAT Gateway -> Not supported
NAT Instance -> Can be used as bastion server
Routing Table
VPCs have an implicit route and main routing table
You can modify the main routing table or create new tables
Each route table contains a local route for the CIDR block
Most specific route for an address wins
Boarder Gateway Protocol
Popular routing protocol for the internet
Propagate information about the network to allow for dynamic routing
Required for Direct connection and optional for VPN
Alternative of not using BGP with AWS VPC is static routes
AWS supports BGP community tagging as a way to control traffic scope and route preference
Required TCP port 179 + ephemeral port
Autonomous System Number (ASN) = Unique endpoint identifier.
Weighting is local to the route and higher weight is preferred path to outbound traffic.
Enhanced Networking
Generally used for high Performance Computing use-cases.
Uses single root I/O virtualisation (SR-IOV) to delivery high performance that traditional virtualised network interfaces.
Might have to install driver if other than Amazon Linux HVM AMI
Intel 82599 VF interface (10 Gbps)
Elastic Network Adapter (25 Gbps)
Placement Groups:
- Clustered
- Spread
Clustered:
Instances are placed into a low-latency group within a single AZ
Used when need low network latency and/or high network throughput
Get the most out of Enhanced networking instances
Finite capacity, recommended launching all you might need up front.
Spread:
Instances spread across underlying hardware fails.
Reduce risk of simultaneous failure if underlying hardware fails.
Can span multiples AZ’s
Max of 7 instance running per groups per AZ.
Route 53
Register domain names.
Check the health of your domain resources.
Routes internet traffic for your domain.
Whats is a DNS?
The Domain Name Systems (DNS) is the phonebook of the Internet. Humans access information online through domain names, like google.com yahoo.com.
DNS record types (A, CNAME, MX, TXT, etc)
- A-Records (Host address)
The A-record is the most basic and the most commonly used DNS record type.
It is used to translate human friendly domain names such as "www.example.com" into IP-addresses such as 23.211.43.53 (machine friendly numbers).
A-records are the DNS server equivalent of the hosts file - a simple domain name to IP-address mapping.
- CNAME-records are domain name aliases.
Computers on the Internet often performs multiple roles such as web-server, ftp-server, chat-server etc.
To mask this, CNAME-records can be used to give a single computer multiple names (aliases).
For example, the computer "computer1.xyz.com" may be both a web-server and an ftp-server, so two CNAME-records are defined:
- TXT-records are used to hold descriptive text.
They are often used to hold general information about a domain name such as who is hosting it, contact person, phone numbers, etc.
One common use of TXT-records is for SPF (see http://www.openspf.org).
- ALIAS-Records (Auto Resolved Alias)
ALIAS-records are virtual alias records resolved by Simple DNS Plus at at the time of each request - providing "flattened" (no CNAME-record chain) synthesized records with data from a hidden source name.
This can be used for different purposes - including solving the classic problem with CNAME-records at the domain apex (for the zone name / for "the naked domain").
Route 53 Concepts (alias, hosted zone, etc)
- MX-Records (Mail exchange)
MX-records are used to specify the e-mail server(s) responsible for a domain name.
Each MX-record points to the name of an e-mail server and holds a preference number for that server.
When sending an e-mail to "user@example.com", your e-mail server must first look up any MX-records for "example.com" to see which e-mail servers handles incoming e-mail for "example.com".
Route 53 Routing Polices
Simple: Simple routing is the most simple and common DNS policy which can accommodate a single FQDN (fully qualified domain name) or IP address. In case of an A record you have to enter the IP address as the value. For load balancers you use CNAME type.
Failover: Failover routing allows you to route traffic to a resource when the resource is healthy and to another resource when the first one is unhealthy.
Geolocation: Geolocation Routing Policy allows the access to the resources based on the geographic location of the users or client.
Latency: You want to return a website’s IP address to client which has lower latency compared to its identical peer hosted in a different AWS Region
Multivalue Answer: Multivalue answer Routing Policy is like Simple Routing Policy but it can return multiple IP addresses associated with an FQDN.
Weighted: Result is returned based on a weight of the DNS record. This is used for distributing the number of sessions equally or unequally among the servers.
Cloud Front:
Distributed content delivery service for simple static asset caching up to 4k live and on-demand video streaming.
CloudFront is integrated with AWS – both physical locations that are directly connected to the AWS global infrastructure, as well as other AWS services. CloudFront works seamlessly with services including AWS Shield for DDoS mitigation, Amazon S3, Elastic Load Balancing or Amazon EC2 as origins for your applications, and Lambda@Edge to run custom code closer to customers’ users and to customize the user experience. Lastly, if you use AWS origins such as Amazon S3, Amazon EC2 or Elastic Load Balancing.
Elastic Load Balance:
Distributed inbound connections to backend endpoints.
Three deferents options:
- Application Load Balancer (Layer 7)
- Network Load Balancer (layer 4)
- Classic Load Balancer (layer 4 or layer 7)
Can be used for public or private network.
Protocols:
ALB: HTTPS, HTTP
NLB: TCP
Classic LB: TCP, SSL, HTTP, HTTPS
Path or Host-based Routing:
ALB: YES
NLB: NO
Classic LB: NO
SSL Offloading:
ALB: YES
NLB: NO
Classic LB: YES
Server Name Indication(SNI)
ALB:YES
NLB: NO
Classic LB: NO
Sticky Session:
ALB:YES
NLB: NO
Classic LB: YES
Static IP, Elastic IP:
ALB:NO
NLB: YES
Classic LB: NO
User Authentication:
ALB:YES
NLB: NO
Classic LB: NO
Application Load Balances:
Classic Load Balancer:
Network Load Balancer:
Concept of Stick Session:
MPLS is an encapsulation protocol used in many service provider and large- scale enterprise networks. Instead of relying on IP lookups to discover a viable "next-hop" at every single router within a path (as in traditional IP networking), MPLS predetermines the path and uses a label swapping push, pop, and swap method to direct the traffic to its destination. This gives the operator significantly more flexibility and enables users to experience a greater SLA by reducing latency and jitter.
Customer Gateway
A customer gateway (CGW) is the anchor on your side of the connection between your network and your Amazon VPC.4 In an MPLS scenario, the CGW can be a customer edge (CE) device located at a Direct Connect location, or it can be a provider edge (PE) device in an MPLS VPN network. For more information on which option best suits your needs, see the Colocation section later in this document.
CIDR = Classless Inter-Domain Routing
WAN = Wide Area Network
MPLS = Multiprotocol Label Switching
References:
- https://simpledns.com/help/dns-record-types
- https://medium.com/tensult/amazon-route-53-routing-policies-cbe356b851d3
- https://data-flair.training/blogs/aws-elb/
- https://www.imperva.com/learn/availability/sticky-session-persistence-and-cookies/
- https://d0.awsstatic.com/whitepapers/aws-amazon-vpc-connectivity-options.pdf
- https://d1.awsstatic.com/whitepapers/Networking/integrating-aws-with-multiprotocol-label-switching.pdf